Using Wireguard VPN to access select LinkORB resources
Team members often require VPN access to select LinkORB services. The purpose of this guide will be to answer the following questions:
Why do I need VPN access, and how do I get it?
For security and audit purposes, certain services at LinkORB are IP-restricted and can only be accessed through a VPN tunnel. Depending on the nature of the resource and your role, your team lead will request VPN access to the appropriate group on your behalf.
Which VPN client should I use?
Once your VPN access request is approved, install the Wireguard VPN client.
How do I configure the VPN client?
Your team lead or another person from the Engineering team will provide VPN settings similar to the below:
[Interface]
Address = 1.1.1.1/11
#DNS = 2.2.2.2, 3.3.3.3
PrivateKey = abcdefghijklmnopqrstuvwxyz=
[Peer]
PublicKey = zyxwvutsrqponmlkjihgfedcba=
PresharedKey = aabbccddeeffgghhiijjkkllmm=
#AllowedIPs = 9.9.9.9/9, ::/9
AllowedIPs = 33.33.33.3/33
AllowedIPs = 44.44.44.3/44
Endpoint = 55.55.55.55:5555
PersistentKeepalive = 25With these settings, you will either configure the VPN client from the graphical user interface (GUI) or the command line interface (CLI) as shown below:
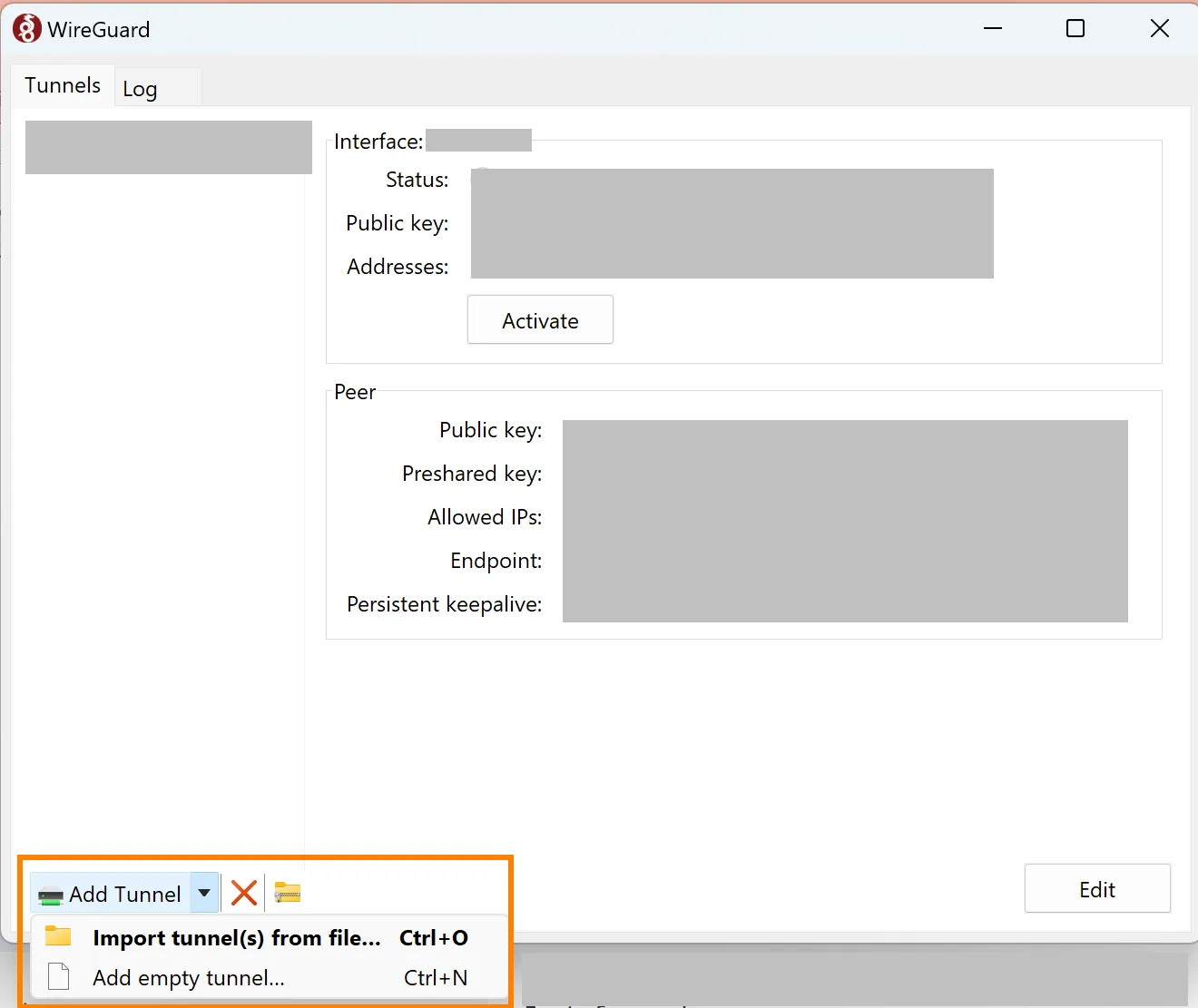
To setup Wireguard from the GUI, you need to either:
- Create a configuration file by:
- Saving the settings to a file named your_LinkORB_alias.conf.
- Importing the file into the Wireguard client.
- Creating an empty tunnel by pasting the provided settings into Wireguard’s tunnel menu.
As shown below, both approaches can be accessed through the Add Tunnel menu found at the bottom left of the Wireguard window.
To setup Wireguard from the command line on Linux:
-
Save the settings to a linkorb0.conf file.
The filename must be a valid Linux network interface name like linkorb0.conf, *wg0.conf, etc.
-
Move the linkorb0.conf file to the /etc/wireguard/ folder.
sudo mv ./linkorb0.conf /etc/wireguard -
Make it so that only users with root access can read or modify the configuration file.
sudo chmod 660 /etc/wireguard/linkorb0.conf -
Start the VPN.
sudo wg-quick up linkorb0
The VPN configuration file contains private keys that could grant a malicious actor access to private LinkORB resources if leaked. To avoid this, delete the VPN configuration (*.conf) file after importing it into WireGuard, or securely store it in a password manager.
Understanding and modifying allowed IPs
The AllowedIPs configuration controls which of your traffic is routed through the VPN. For example, the below setting will route all traffic through the VPN.
AllowedIPs = 0.0.0.0/0If you’ve configured Wireguard to route all traffic through the VPN, we recommend activating your VPN tunnel during work hours and Deactivating it when you’re not working.
Alternatively, a configuration like the one below with multiple distinct IPs only routes traffic to the services on those IPs through the VPN.
#AllowedIPs = 9.9.9.9/9, ::/9
AllowedIPs = 33.33.33.3/33
AllowedIPs = 44.44.44.3/44Under this configuration, the VPN tunnel can remain active at all times, as only targeted traffic is affected.
As shown above, comments (#) are supported in configuration files.
As new LinkORB services are created or your access needs change, team members may need to insert additional AllowedIPs into the configuration file.
Modifying allowed IPs
To modify the VPN tunnel’s configuration from Wireguard’s GUI, select the target tunnel in the left menu and then select Edit on the bottom right.
This will allow the insertion of additional AllowedIPs or commenting out of existing IPs. Click Save after making the desired changes.
If you have configured Wireguard from the command line, add or remove the specific IPs to/from the linkorb0.conf file and restart the VPN tunnel.
When should I not use the VPN?
When configured to route all traffic over the VPN, deactivating the tunnel during video chats will improve the quality of the call. Similarly, deactivating the tunnel outside of working hours will provide a better experience while you game 🎮 or stream 📺.
Finally, some LinkORB services display more detailed error messages when connecting through the VPN. When it is necessary to view error messages from an end-user perspective, team members should deactivate the tunnel.
Can I use the VPN on public Wi-Fi?
Activating the VPN tunnel is useful when using public Wi-Fi or if you have a restrictive internet provider.
What if I already use a VPN?
As stated, select LinkORB resources are only accessible through a properly configured Wireguard client.
If you require the use of an existing VPN client such as Open VPN and Wireguard simultaneously, try the following:
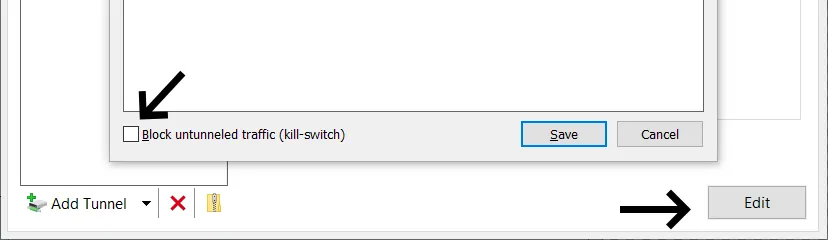
- In Wireguard, select the target tunnel in the left menu and then select Edit on the bottom right
- Set
AllowedIPs = 0.0.0.0/0as the only allowed IP. - Toggle on the Block untunneled traffic (kill switch) option in the bottom left
- Click Save
Can I transfer the VPN to a different computer?
You may transfer the provided VPN configuration to a different computer through a secure channel such as a password manager or in the encrypted format that it was sent to you.
Our security policy requires that you either:
- Name: Security (
#security)